
In the realm of online privacy, the Tor Browser stands as a fortress. This article unravels the intricacies of Tor, shedding light on its safety, functionality, and the art of navigating the elusive dark web. Discover the wonders of Tor, explore its working mechanism, and decide whether it’s the right fit for you. For a seamless and secure browsing experience, delve into the realm of Avast Secure Browser.
Understanding Tor Browser: A Cloak for Your Online Presence
What Sets Tor Browser Apart?
Tor, short for The Onion Router, revolutionizes web browsing by ensuring complete anonymity. By concealing your IP address and routing web traffic through a labyrinth of nodes, Tor caters to the privacy needs of whistleblowers, journalists, and anyone craving online discretion.
The Intricacies of Tor’s Operation
Tor employs onion routing, an encryption technique originating from the US Navy. This technique involves transmitting data through a series of nodes, peeling away layers of encryption at each stop. This complex process creates an impenetrable shield, making Tor the epitome of a dark web browser.
Navigating the Layers: How Tor Encrypts Your Web Traffic
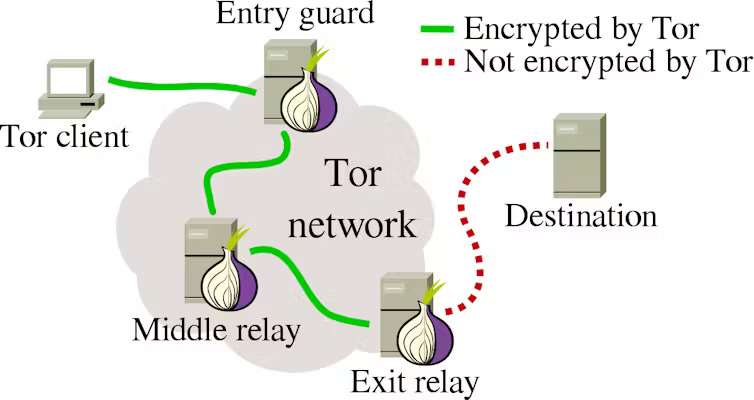
Decoding Tor’s Three-Layered Network
- Entry/Guard Node: Initiates your data into the Tor circuit, acting as the first line of defense.
- Middle Nodes: Fully encrypt your data, ensuring that each node knows only its predecessors and successors for maximum anonymity.
- Exit Node: Unveils the decrypted data, allowing it to reach its final destination while maintaining privacy.
Simplifying Tor’s Complexity
Despite its sophisticated operation, utilizing Tor Browser doesn’t demand a Ph.D. in computer science. Its user-friendly interface makes it accessible to all, proving that privacy doesn’t have to be complicated.
Unmasking Tor’s Magic: Does It Truly Hide Your IP?
The Wizardry of Onion Routing
Tor’s onion routing technology not only hides your IP address but also adds an extra layer of multi-faceted encryption. With over 7,000 independent network relays, Tor ensures your internet traffic remains a mystery until it reaches its destination.
The Veil of Anonymity: Is Tor Browser Truly Anonymous?
While Tor successfully conceals your location and browsing activities, it comes with limitations. Your ISP can detect Tor usage, and providing personal details online can compromise your identity.
Tor vs. Proxy: Unraveling the Distinctions
Tor Browser vs. Proxy Server
Unlike proxy servers, Tor Browser combines IP address hiding with robust encryption, providing superior privacy protection. While proxies merely conceal your IP, Tor goes the extra mile to safeguard your data from potential threats.
Choosing Your Privacy Arsenal: VPN vs. Tor vs. Proxy
Deciding between a VPN, proxy, or Tor depends on your specific needs. Each tool has its strengths, and understanding them ensures you pick the right ally for your online privacy battles.
The Dance of Tor and VPN: A Synchronized Symphony

Tor vs. VPN: Unveiling the Differences
Tor and VPNs share the goal of encrypting and rerouting web traffic, yet their approaches differ. While VPNs operate through central service providers, Tor’s decentralized network, run by volunteers, offers a distinct path to online anonymity.
Fortifying Your Defenses: Using Tor with a VPN
Combining Tor with a VPN provides an extra layer of protection. This collaboration ensures end-to-end encryption, shielding your web traffic from prying eyes at entry and exit nodes.
Peering into the Shadows: The Many Faces of Tor Browser
The Multifaceted Usage of Tor
Tor Browser finds its primary purpose in anonymous browsing, serving a diverse user base, including journalists, activists, and privacy-conscious individuals. However, it also attracts the attention of criminals seeking refuge in its anonymity.
Tracking in the Shadows: Can You Be Traced on Tor?
Despite Tor’s robust privacy features, tracking remains a possibility. Pairing Tor with a VPN strengthens its weak points, offering comprehensive protection against potential threats.
Embracing Tor: Reasons to Make It Your Privacy Ally
The Allure of Tor’s Privacy
Tor’s onion network not only ensures privacy but also boasts open-source accessibility. Its simplicity and effectiveness make it an ideal choice for those valuing online privacy and data security.
The Legal Landscape: Is Tor Browser Aboveboard?
While Tor is legal in most countries, its association with the dark web may attract unnecessary attention. Users should be aware of potential throttling by ISPs and government monitoring, depending on their location.
Safety in the Shadows: Assessing Tor Browser’s Security
Despite some vulnerabilities, Tor Browser remains generally safe. Augmenting its security with a VPN, firewall, and robust antivirus software ensures a fortified defense against online threats.
Tor Browser and the Enigmatic Dark Web
Beyond the Surface: Tor’s Link to the Dark Web
The Tor Browser’s synonymous connection with the dark web originated with the Silk Road. While the dark web harbors both legal and illicit activities, Tor’s design emphasizes online privacy and security.
The Downsides of Tor Browser: Balancing Privacy and Vulnerabilities
Tor, despite its prowess, comes with drawbacks. Its slower speeds, perceived stigma, susceptibility to blocking, and vulnerabilities at entry and exit nodes pose challenges that users must consider.
Exploring Alternatives: Other Dark Web Browsers
Beyond Tor: Exploring Alternatives
While Tor dominates dark web access, other browsers offer unique advantages:
- Subgraph OS: Resistant to surveillance, recommended by whistleblower Edward Snowden.
- Firefox: Popular but lacks robust safety features.
- Waterfox: A fast Firefox-based browser with privacy protection.
- I2P – Invisible Internet Project: A fully encrypted, private network layer.
Mastering Tor: A Step-by-Step Guide for Windows and Mac
Bringing Tor to Your Desktop
- Visit the Tor project website’s download page.
- Download the Tor Browser for your operating system.
- Install the application on your device.
- Launch Tor Browser and connect to the Tor network for a secure browsing experience.
Tor on the Go: Using Tor Browser on Mobile
Mobile Tor for Android Users
- Visit the Tor project website or the Google Play store.
- Download the Tor Browser app.
- Install the app on your Android device.
- Launch the browser for secure and private online exploration.
Elevate Your Privacy: Avast Secure Browser as Your Ally
For those seeking a user-friendly, secure alternative to Tor, the Avast Secure Browser stands out. Light, fast, and easy-to-use, it provides robust online privacy, thwarting hackers, blocking malicious links, and warning against dangerous websites. Download Avast Secure Browser today for an unparalleled online security experience.
FAQs
Q: Is Tor Browser illegal to use? Tor Browser is legal in most countries. Its primary purpose is to enhance user privacy and security. However, be aware of your local laws and regulations to ensure responsible usage.
Q: Can I use Tor Browser on my smartphone? Yes, Tor Browser is available for Android devices. You can download it from the official website or reputable app stores.
Q: Does Tor Browser slow down internet speed? Due to its unique routing process, Tor Browser may slow down your internet speed. However, the trade-off is enhanced privacy and security.
Q: Is Tor Browser the only way to access the Dark Web? Tor Browser is a common tool for accessing the Dark Web, but it’s not the only way. Other methods exist, but Tor remains a popular choice for its security features.
Q: How frequently should I update Tor Browser? Regularly updating Tor Browser is crucial for maintaining security. Check for updates at least once a month or enable automatic updates for seamless protection.
Q: Can I use Tor Browser for everyday browsing? While Tor Browser provides enhanced privacy, it may not be suitable for everyday browsing due to slower speeds. Reserve its use for activities where privacy is paramount.


